DALLAS — Watch the full story tonight on WFAA News at 10.
Judson School Superintendent Jeanette Ball says she will never forget the 4:30 a.m. phone call this past June.
Her assistant superintendent of technology told Ball the school district had been attacked by ransomware.
“What do you mean?” Ball recalled asking. "We’re not going to have internet this morning at work?"
“No, Dr. Ball, it’s really bad,” the assistant superintendent told her.
The Judson Independent School District’s nightmare had begun. The district serves 23,000 students in the San Antonio area.
Ransomware hackers had taken down the school district’s electronic systems: phones, Wi-Fi, computers, fax machines, electronic badges for doors.
Locked out of its computer systems for weeks, Ball worried that the district wouldn’t be able to pay thousands of Judson ISD employees. She said parents couldn’t get transcripts for graduating seniors headed off to college. The district even cancelled summer school for two days.
“We had no phones, so we couldn’t call each other to tell people what was going on,” Ball told WFAA. “Just think of being truly isolated from the world.”

Judson is among more than two dozen Texas districts hit by a wave of ransomware attacks since 2019. The North Texas districts include Fort Worth, Athens, Lancaster and Allen.
A nationwide problem
Brett Callow, a threat analyst with cybersecurity company Emsisoft, tracks school district ransomware attacks. Nationwide, he’s tracked 58 school districts that reported attacks in 2020, and more than 55 so far this year.
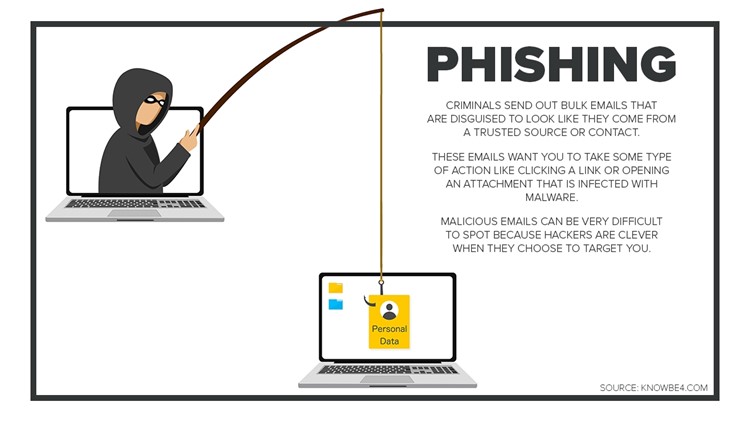
The way hackers get access to a supposedly secure system is often as simple as clicking on a link in an email. Hackers have become adept at sending “phishing” emails that look legitimate, and tricking unsuspecting victims into clicking on a link.
Ransomware attackers infiltrate a school district’s computers, lock up the district’s systems, steal valuable personal data of staff and students - and hold it for ransom.


If they’re not paid, they sell or post the stolen data on the “dark web” – a portion of the internet not accessible by traditional search engines that serves as a hidden marketplace often used by crooks.
Local school leaders are already under pressure from pandemic learning losses and strained budgets. Now, they are finding themselves victims of this new cyber threat to their staffs’ and students’ sensitive data, requiring them to manage how to inform the public, and whether to pay a ransom to criminals.
Judson, for example, ultimately paid $547,000 out of school funds to the hackers – the largest known ransom paid by any school district in the country. Other school districts contacted by WFAA declined on-camera interviews to discuss details of their ransomware attacks.
“These bad actors are very good at what they do,” said State Rep. Giovanni Capriglione, chair of the Texas House Innovation and Technology Caucus. “In some of these cases, you’re literally going against the nation-state.”
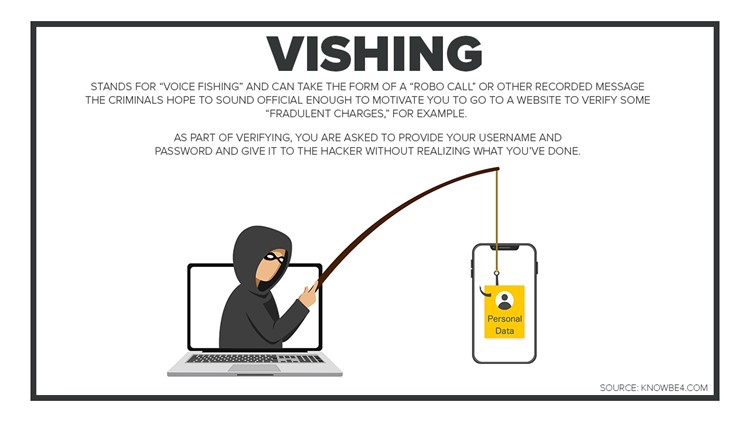
How do hackers gain access to your information?
Allen
In September, the 21,000-student Allen Independent School District became one of the latest ransomware victims. The district alerted parents in a Sept. 23 email that, days earlier, it had experienced “network outages that impacted several systems, including Wi-Fi, printers and phones.”
“The Allen ISD Technology Department discovered the outage was due to a cybersecurity threat,” the school email said.
On Oct. 4, parents began getting emails – from the hackers.
“Staff and parents of Allen ISD, Howdy!” one email began. “We see that Allen ISD very like to talk through press, so we will support this initiative!”
The hackers claimed in the email that they’d been in the district’s network for months.
“We had a ton of time to carefully study, exfiltrate the data and prepare attack,” the email said. “By the way nobody tried to stop the attack. IT was sleeping very well.”
The email says hackers provided the school district proof, showing the volume of data taken from the network. But the district had not paid a ransom, the email said.
“So we can make a conclusion that they really don't care what happen to personal info after it is stored in their system,” the email said.
The hackers gave the district five days to pay the unspecified ransom, or the demand would be increased to $10 million.
“The attackers likely emailed parents in the hope that they would put pressure on the district to pay,” said Callow, the threat analyst from Emsisoft. “This is not the only gang to use the tactic.”
Allen ISD announced in a statement to parents that it had “no intention of paying.”
An Allen parent, who provided WFAA an email from hackers, said he was shocked when the email hit his inbox. He is certain that his son’s personal information has been compromised. He believes the hackers gained access to his email by accessing his son’s school profile.
In October, a hacking group claimed credit on Twitter for the Allen hack. Twitter quickly disabled the hacking group’s Twitter handle. Sources also provided WFAA screenshots showing that the group had posted a few of Allen’s files on an encrypted cloud storage site.
On its blog on the dark web, the group threatened that hacker targets that don’t pay for its “bug hunting work” will find part of their information “for sale” and “part will be free for downloads.”
“I agree we shouldn't pay them,” the Allen parent told WFAA.
The parent asked WFAA to conceal his identity because his wife works for the district. At this point, he said, he believes the hackers have been far more transparent about the incident than the district.
“I know more from the hackers than from Allen ISD,” he said.
In an Oct. 12 statement, Allen ISD said it knew “some private staff data was obtained but have not seen any evidence that student or parent private information was involved in this incident.” The district also announced that it was offering a credit monitoring program for adults, and identity protection for minors.
Allen ISD officials declined a WFAA interview request. When asked about the hacking group that had claimed responsibility, the district’s chief spokesman replied, “We are aware of the group and those files.”
Lancaster
Lancaster ISD – with an enrollment of over 7,000 students – acknowledged it was hacked back in June.
Sources provided WFAA screenshots from the hacking group.
“The network of Lancaster Independent School District was screwed, and now we have about 9 GB data from file servers,” the hackers posted on their dark web site.
The hackers ultimately posted thousands of pages of Lancaster ISD’s stolen internal records, including personnel files containing Social Security numbers and other sensitive information.
The district acknowledged the cyber breach but didn’t reveal that hackers posted sensitive records to the dark web.
“Common courtesy should dictate that they inform an employee of what data has been confiscated,” Martin Yarborough, a North Texas cybersecurity expert and former Fort Worth ISD chief information officer.


On Its site, the hackers posted a log of what it said was its communications with district officials.
The hacker is asked: “Why did you already publish our data on your site? We are trying to figure out what to do and were working on how much we could possibly pay and now our data is up.”
The response: “You need to pay or we continue publishing data.”
The chat continues for more than a week and ends with the person asking the hackers: “Are you going to work with us? You already posted the data so the value you’re asking is decreasing.”
The response: “No.”
Lancaster officials declined to comment, citing the ongoing investigation.
The district did not pay the ransom.
The group kept posting Lancaster’s files.
Hacked district names not public?
By law, districts must notify parents if student information may have been compromised. But there is no similar rule that they are required to tell employees.
Over the summer, the Texas Education Agency released a list of more than 70 districts that reported cybersecurity breaches since 2019. However, when WFAA asked for an updated list in September, TEA denied the request.
TEA said it had “become apparent that such disclosure may hinder a school district’s response to an ongoing cyberattack or other cybersecurity incident” and “make the reporting school districts more vulnerable to future attacks.”
The agency asked for the Texas Attorney General’s office to determine if the names of hacked districts should be public information.
Judson ISD’s superintendent was the only school official who would discuss details about their particular district’s ransomware attack.
Superintendent Ball said the district’s technology staff worked frenetically around the clock to get the payroll system working. But even then, Judson ISD struggled to find a bank that would cut the checks. Banks were afraid to do business with the district fearing hackers would “worm” their way into their financial systems.
Payroll ultimately did go out on time. Ball credits the district’s technology team for making it happen.
The district had cyber insurance, which it used to hire a company to negotiate with the hacker and monitor the dark web. Before the district agreed to pay a ransom, the hackers had to prove that they had sensitive information belonging to the district and that none of it had been posted.
“Once we knew that they had some information that was probably not something we would want out there, then the decision was made that we would pay,” Ball said.
Judson ultimately paid $547,000 out of school funds to the hackers. Ball said she and the board felt the district owed it to district employees to protect their personal information, such as Social Security numbers.
“If I would ask you to put your Social Security number, your driver’s license number, your birthday on a billboard, you’d probably tell me … 'no, Jeanette, I’m not going to do that,'” Ball said. “So why would I do that to somebody else? Putting it out on the dark web is what I would be doing, and I’m not willing to risk that.”
Ball said the ransom cut into funds the district planned to use to fill learning gaps caused by the pandemic. Now, they will have to find other ways to address the issue.
Experts: paying ransom = bad idea
Cybersecurity experts say paying ransoms – either directly or indirectly – is a bad idea.
“The data’s valuable,” said Yarborough, the North Texas cybersecurity expert. “They’ll keep that data. They may give you back a copy, but they’re going to keep a copy of the data.”
State Rep. Capriglione filed a bill last session that would have forbidden state and local governments from paying ransoms. He says he got a lot of push back from Texas officials who wanted the discretion to pay to unlock their systems and get their data back.


“Let's just be frank, you're giving money to criminals, right?” State Rep. Capriglione said. “It becomes easy to just pay them off instead of doing what I think is the better tactic, which is to improve your systems.”
There is currently no legal requirement that government agencies publicly report ransom payments.
WFAA discovered that one state educational agency serving San Antonio-area school districts had been hacked, had a ransom paid, but didn’t make it public.
When contacted, a spokeswoman for Education Service Center Region 20 agreed to answer questions, but asked that WFAA not reveal the center’s identity. She said that could open up ESC 20 to additional attacks. WFAA declined because ESC 20 is a government agency accountable to the public.
In an email statement, ESC’s 20 spokeswoman said it had discovered that its systems “were encrypted by ransomware” on Dec. 26, 2020.
“Ultimately, this incident impacted approximately 90% of ESC 20’s systems including its backups,” ESC 20’s spokesperson said in an email. “Our insurance carrier … paid to gain access to our data and restore our systems.”
ESC 20 initially declined to reveal the amount of the ransom, and only did so when WFAA filed an open records request.
The amount paid? $600,000.
ESC 20’s systems were not fully restored until late February.
State Rep. Capriglione says he plans to sponsor legislation that requires better transparency from government entities.
“We understand that sometimes bad stuff happens to even good groups,” he said. “But that doesn’t absolve anyone of the responsibility - a government official or an elected official - to let everyone know what happened.”
He believes ransoms – whether paid directly or indirectly – should be publicly reported as a matter of law.
Increasingly, more and more organizations are getting cyber insurance to deal with cybersecurity breaches. But Callow of Emisoft says cyber insurance can be a “double-edged sword.”
Because while it may insulate organizations from the cost of an attack, Callow said some hackers may believe that insured organizations are more likely to pay “if the money isn’t coming from their own pocket.”
Email investigates@wfaa.com